A VPN from the trusted pioneer in internet privacy.
We currently offer Mozilla VPN in the US, the UK, Canada, New Zealand, Singapore and Malaysia.
Available now: Windows 10, Android & iOS
Coming soon: Mac & Linux
Available for Windows™ PC, Mac®, iOS and Android™ devices: Norton Secure VPN is compatible with PCs, Mac, Android smartphones and tablets, iPads, and iPhones. Norton Secure VPN may be used on the specified number of devices – with unlimited use during the subscription term. On MAC we use OpenVPN® Protocol which ensures maximum security and speed! Urban VPN for MAC is optimized for privacy, high speed, unlimited bandwidth and a secure connection to hide your IP. On top of that, it's completely free!
One tap to privacy
We use the most advanced protocol, WireGuard®, to encrypt your network activity and hide your IP address.
Fast network speed
Surf, stream, game, and get work done with fast network speed using our WireGuard® powered servers.
Your privacy comes first
We don't store your online activity logs on our servers.
US$4.99/month
- Device-level encryption
- 280+ servers in 30+ countries
- No bandwidth restrictions
- No logging of your network activity
- Connect up to 5 devices
We currently offer Mozilla VPN in the US, the UK, Canada, New Zealand, Singapore and Malaysia.
Available in 6 countries now. More regions coming soon.
We currently offer Mozilla VPN in the US, the UK, Canada, New Zealand, Singapore and Malaysia.
About our trusted partner
The Mozilla VPN runs on a global network of servers powered by Mullvad using the WireGuard® protocol. Mullvad puts your privacy first and does not keep logs of any kind.
The new VPN clients are compatible with Android (version 6 and up), Windows 10 (64 bit), and iOS. Mac and Linux clients are coming soon.
We don't log, track, or share any of your network activity. We adhere strictly to Mozilla's Data Privacy Principles, and we only collect the most minimal data required to keep the VPN healthy and operational.
WireGuard® protocol encrypts your network traffic protecting all your private information. Compared to existing VPN protocols, WireGuard's lightweight code is easier for security analysts to review and audit - making it a more secure option for the VPN. In addition, your online activities can stay anonymous because we never log, track or share your network data.
You can get your money back within 30-days of purchasing the subscription. Contact us and submit the refund request by tapping the Get Help button in Settings on your app.

This article outlines instructions to configure a client VPN connection on commonly-used operating systems. For more information about client VPN, please refer to our Client VPN Overviewdocumentation.
For troubleshooting, please refer to our Troubleshooting Client VPN documentation.
Android
To configure an Android device to connect to the Client VPN, follow these steps:
- Navigate to Settings -> Wireless & Networks -> VPN
- Click the Plus Icon to add an additional VPN profile
Do You Need A Vpn For Mac
Name: This can be anything you want to name this connection, for example, 'Work VPN.'
Type: select L2TP/IPSEC PSK
Server address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
IPSec pre-shared key: Enter the pre-shared key that admin created in Security appliance >Configure > Client VPN settings.
IP Cam Pro for Mac OS X. IP Cam Pro turns your mac into a IP surveillance camera. Run IP Cam Pro on your mac, and via Wi-Fi network, you can view live images captured by your mac's built in FaceTime camera (or any mac compatible USB/Firewire camera) on web browser from any computer. IP Cam for Mac OS X. IP Cam turns your mac into a IP surveillance camera. Run IP Cam on your mac, and via Wi-Fi network, you can view live images captured by your mac's built in FaceTime camera (or any mac compatible USB/Firewire camera) on web browser from any computer. You can even view IP Cam using Safari browser from another mobile device such as iPhone, iPad or iPod Touch. Video recognition requires intensive processing by your computer. The minimum requirements for a single IP camera at QVGA are: Mac OS X 10.10 or higher. 2.0GHz Intel-based processor or higher. 2GB RAM or higher. Minimum screen resolution of 1024x768. At least 25GB of free disk space per camera is. Ip cam viewer mac os x free.
Press save
You will be prompted for user credentials when you connect.
Chrome OS
Chrome OS based devices can be configured to connect to the Client VPN feature on MX Security Appliances. This allows remote users to securely connect to the LAN. This article will cover how to configure the VPN connection on a Chrome OS device. For more information on how to setup the Client VPN feature of the MX or how to connect from other operating systems, please visit the MX documentation.
- If you haven't already, sign in to your Chromebook.
- Click the status area at the bottom of your screen, where your account picture is located.
- Select Settings.
- In the 'Internet connection' section, click Add connection.
- Select Add private network.
- In the box that appears, fill in the information below:
- Server hostname:Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Service name: This can be anything you want to name this connection, for example, 'Work VPN.'
- Provider type: Select L2TP/IPsec + Pre-shared key.
- Pre-shared key: Enter shared secret that admin created in Security appliance >Configure > Client VPN settings.
- Username credentials for connecting to VPN. If using Meraki authentication, this will be an e-mail address.
- Password credentials for connecting to VPN.
- Click Connect.
For more information regarding the configuration of VPN connections in Chrome OS, visit the Google Support page.
To configure an iOS device to connect to the Client VPN, follow these steps:
- Navigate to Settings -> General-> VPN -> Add VPN Configuration..
- Type: set to L2TP.
- Description:This can be anything you want to name this connection, for example, 'Work VPN.'
- Server: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Account: Enter the username
- Password: Enter if desired. If the password is left blank, it will need to be entered each time the device attempts to connect to the Client VPN.
- Secret: Enter shared secret that admin created in Security appliance >Configure > Client VPN settings.
- Ensure that Send All Traffic is set to On.
- Save the configuration.
macOS
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, VPN account/user name setting on client devices (e.g., PC or Mac) is the user email address entered in the Dashboard.
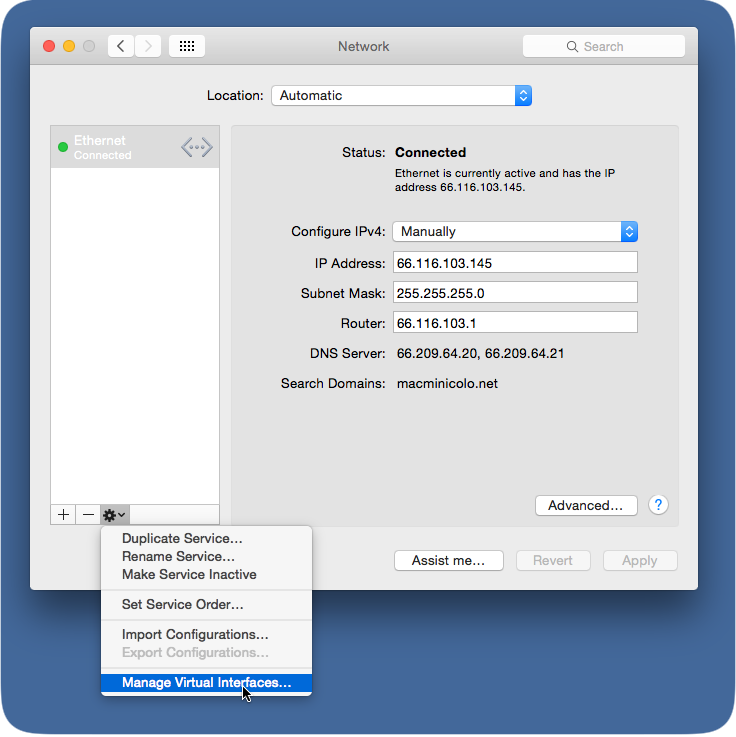
The instructions below are tested on Mac OS 10.7.3 (Lion).
Open System Preferences > Network from Mac applications menu. Click the '+' button to create a new service, then select VPN as the interface type, and choose L2TP over IPsec from the pull-down menu.
- Server Address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Account Name: Enter the account name of the user (based on AD, RADIUS or Meraki Cloud authentication).
- User Authentication > Password: User password (based on AD, RADIUS or Meraki Cloud authentication).
- Machine Authentication > Shared Secret: Enter shared secret that admin created in Security appliance >Configure > Client VPN settings.
The VPN connectivity will not be established if you don't enable the Send all traffic over VPN connection option!
Windows 7
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, VPN account/user name setting on client devices (e.g., PC or Mac) is the user email address entered in the Dashboard.
Open Start Menu > Control Panel, click on Network and Internet, click on View network status and tasks.
In the Set up a connection or network pop-up window, choose Connect to a workplace (Set up a dial-up or VPN connection to your workplace).
Choose Use my Internet connection (VPN), in the Connect to a workspace dialog window.
In the Connect to a Workplace dialog box, enter:
- Internet address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Destination name:This can be anything you want to name this connection, for example, 'Work VPN.'
Choose 'Don't connect now; just set it up so that I can connect later' option.
Click Next. In the next dialog window, enter the user credentials, and click Create.

Despite the name 'Unencrypted PAP', the client's password is sent encrypted over an IPsec tunnel between the client device and the MX. The password is fully secure and never sent in clear text over either the WAN or the LAN.
Windows 8
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, VPN account/user name setting on client devices (e.g., PC or Mac) is the user email address entered in the Dashboard.
Open Start Menu > Network and Sharing Center and click Settings.
In the Set Up a Connection or Network pop-up window, choose Connect to a workplace.
(Set up a dial-up or VPN connection to your workplace).
Choose Use my Internet connection (VPN), in the Connect to a Workspace dialog window.
In the Connect to a Workplace dialog box, enter:
- Internet address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Destination name:This can be anything you want to name this connection, for example, 'Work VPN.'
Go back to Network and Sharing Center and click Change Adapter Settings.
Despite the name 'Unencrypted PAP', the client's password is sent encrypted over an IPsec tunnel between the client device and the MX. The password is fully secure and never sent in clear text over either the WAN or the LAN.
Windows 10
Currently only the following authentication mechanisms are supported: Gramblr for mac free download.
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, VPN account/user name setting on client devices (e.g., PC or Mac) is the user email address entered in the Dashboard.
Open Start Menu > Search 'VPN' > Click Change virtual private networks (VPN)
From the VPN settings page, click Add a VPN connection.
In the Add a VPN connection dialog:
- VPN provider: Set to Windows (built-in)
- Connection name: This can be anything you want to name this connection, for example, 'Work VPN.'
- Server name or address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- VPN type: Select L2TP/IPsec with pre-shared key
- User name and Password: optional
Press Save.
After the VPN connection has been created, click Change adapter options under Related settings.
Right-click on the VPN Connection from the list of adapters and click Properties.
Despite the name 'Unencrypted PAP', the client's password is sent encrypted over an IPsec tunnel between the client device and the MX. The password is fully secure and never sent in clear text over either the WAN or the LAN.
In Advanced Properties dialog box, choose 'Use preshared key for authentication' and enter the pre-shared key that admin created in Security appliance >Configure > Client VPN settings.
Back at the Network Connections window, right-click on the VPN connection and click Connect / Disconnect.

Find your VPN profile and click Connect.
Windows XP
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, use the email address for VPN account / user name.
Open Start Menu > Control Panel, click on Network Connections.
In the Network Tasks section, click on Create a new connection.
Choose Connect to the network at my workplace, in the New Connection Wizard window.
Choose Virtual Private Network connection in the next section.
Then, give a name for this connection. This can be anything you want to name this connection, for example, 'Work VPN.'
Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
In the Connect box, click on Properties
In the General tab, verify the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
Surf, stream, game, and get work done with fast network speed using our WireGuard® powered servers.
Your privacy comes first
We don't store your online activity logs on our servers.
US$4.99/month
- Device-level encryption
- 280+ servers in 30+ countries
- No bandwidth restrictions
- No logging of your network activity
- Connect up to 5 devices
We currently offer Mozilla VPN in the US, the UK, Canada, New Zealand, Singapore and Malaysia.
Available in 6 countries now. More regions coming soon.
We currently offer Mozilla VPN in the US, the UK, Canada, New Zealand, Singapore and Malaysia.
About our trusted partner
The Mozilla VPN runs on a global network of servers powered by Mullvad using the WireGuard® protocol. Mullvad puts your privacy first and does not keep logs of any kind.
The new VPN clients are compatible with Android (version 6 and up), Windows 10 (64 bit), and iOS. Mac and Linux clients are coming soon.
We don't log, track, or share any of your network activity. We adhere strictly to Mozilla's Data Privacy Principles, and we only collect the most minimal data required to keep the VPN healthy and operational.
WireGuard® protocol encrypts your network traffic protecting all your private information. Compared to existing VPN protocols, WireGuard's lightweight code is easier for security analysts to review and audit - making it a more secure option for the VPN. In addition, your online activities can stay anonymous because we never log, track or share your network data.
You can get your money back within 30-days of purchasing the subscription. Contact us and submit the refund request by tapping the Get Help button in Settings on your app.
This article outlines instructions to configure a client VPN connection on commonly-used operating systems. For more information about client VPN, please refer to our Client VPN Overviewdocumentation.
For troubleshooting, please refer to our Troubleshooting Client VPN documentation.
Android
To configure an Android device to connect to the Client VPN, follow these steps:
- Navigate to Settings -> Wireless & Networks -> VPN
- Click the Plus Icon to add an additional VPN profile
Do You Need A Vpn For Mac
Name: This can be anything you want to name this connection, for example, 'Work VPN.'
Type: select L2TP/IPSEC PSK
Server address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
IPSec pre-shared key: Enter the pre-shared key that admin created in Security appliance >Configure > Client VPN settings.
IP Cam Pro for Mac OS X. IP Cam Pro turns your mac into a IP surveillance camera. Run IP Cam Pro on your mac, and via Wi-Fi network, you can view live images captured by your mac's built in FaceTime camera (or any mac compatible USB/Firewire camera) on web browser from any computer. IP Cam for Mac OS X. IP Cam turns your mac into a IP surveillance camera. Run IP Cam on your mac, and via Wi-Fi network, you can view live images captured by your mac's built in FaceTime camera (or any mac compatible USB/Firewire camera) on web browser from any computer. You can even view IP Cam using Safari browser from another mobile device such as iPhone, iPad or iPod Touch. Video recognition requires intensive processing by your computer. The minimum requirements for a single IP camera at QVGA are: Mac OS X 10.10 or higher. 2.0GHz Intel-based processor or higher. 2GB RAM or higher. Minimum screen resolution of 1024x768. At least 25GB of free disk space per camera is. Ip cam viewer mac os x free.
Press save
You will be prompted for user credentials when you connect.
Chrome OS
Chrome OS based devices can be configured to connect to the Client VPN feature on MX Security Appliances. This allows remote users to securely connect to the LAN. This article will cover how to configure the VPN connection on a Chrome OS device. For more information on how to setup the Client VPN feature of the MX or how to connect from other operating systems, please visit the MX documentation.
- If you haven't already, sign in to your Chromebook.
- Click the status area at the bottom of your screen, where your account picture is located.
- Select Settings.
- In the 'Internet connection' section, click Add connection.
- Select Add private network.
- In the box that appears, fill in the information below:
- Server hostname:Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Service name: This can be anything you want to name this connection, for example, 'Work VPN.'
- Provider type: Select L2TP/IPsec + Pre-shared key.
- Pre-shared key: Enter shared secret that admin created in Security appliance >Configure > Client VPN settings.
- Username credentials for connecting to VPN. If using Meraki authentication, this will be an e-mail address.
- Password credentials for connecting to VPN.
- Click Connect.
For more information regarding the configuration of VPN connections in Chrome OS, visit the Google Support page.
To configure an iOS device to connect to the Client VPN, follow these steps:
- Navigate to Settings -> General-> VPN -> Add VPN Configuration..
- Type: set to L2TP.
- Description:This can be anything you want to name this connection, for example, 'Work VPN.'
- Server: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Account: Enter the username
- Password: Enter if desired. If the password is left blank, it will need to be entered each time the device attempts to connect to the Client VPN.
- Secret: Enter shared secret that admin created in Security appliance >Configure > Client VPN settings.
- Ensure that Send All Traffic is set to On.
- Save the configuration.
macOS
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, VPN account/user name setting on client devices (e.g., PC or Mac) is the user email address entered in the Dashboard.
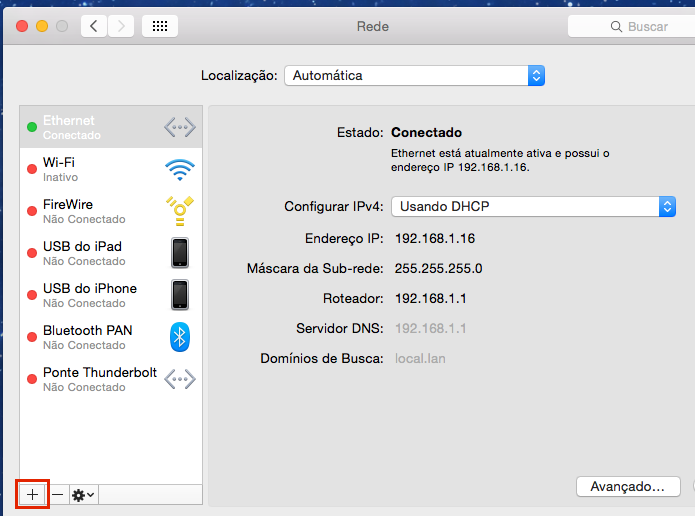
The instructions below are tested on Mac OS 10.7.3 (Lion).
Open System Preferences > Network from Mac applications menu. Click the '+' button to create a new service, then select VPN as the interface type, and choose L2TP over IPsec from the pull-down menu.
- Server Address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Account Name: Enter the account name of the user (based on AD, RADIUS or Meraki Cloud authentication).
- User Authentication > Password: User password (based on AD, RADIUS or Meraki Cloud authentication).
- Machine Authentication > Shared Secret: Enter shared secret that admin created in Security appliance >Configure > Client VPN settings.
The VPN connectivity will not be established if you don't enable the Send all traffic over VPN connection option!
Windows 7
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, VPN account/user name setting on client devices (e.g., PC or Mac) is the user email address entered in the Dashboard.
Open Start Menu > Control Panel, click on Network and Internet, click on View network status and tasks.
In the Set up a connection or network pop-up window, choose Connect to a workplace (Set up a dial-up or VPN connection to your workplace).
Choose Use my Internet connection (VPN), in the Connect to a workspace dialog window.
In the Connect to a Workplace dialog box, enter:
- Internet address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Destination name:This can be anything you want to name this connection, for example, 'Work VPN.'
Choose 'Don't connect now; just set it up so that I can connect later' option.
Click Next. In the next dialog window, enter the user credentials, and click Create.
Despite the name 'Unencrypted PAP', the client's password is sent encrypted over an IPsec tunnel between the client device and the MX. The password is fully secure and never sent in clear text over either the WAN or the LAN.
Windows 8
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, VPN account/user name setting on client devices (e.g., PC or Mac) is the user email address entered in the Dashboard.
Open Start Menu > Network and Sharing Center and click Settings.
In the Set Up a Connection or Network pop-up window, choose Connect to a workplace.
(Set up a dial-up or VPN connection to your workplace).
Choose Use my Internet connection (VPN), in the Connect to a Workspace dialog window.
In the Connect to a Workplace dialog box, enter:
- Internet address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Destination name:This can be anything you want to name this connection, for example, 'Work VPN.'
Go back to Network and Sharing Center and click Change Adapter Settings.
Despite the name 'Unencrypted PAP', the client's password is sent encrypted over an IPsec tunnel between the client device and the MX. The password is fully secure and never sent in clear text over either the WAN or the LAN.
Windows 10
Currently only the following authentication mechanisms are supported: Gramblr for mac free download.
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, VPN account/user name setting on client devices (e.g., PC or Mac) is the user email address entered in the Dashboard.
Open Start Menu > Search 'VPN' > Click Change virtual private networks (VPN)
From the VPN settings page, click Add a VPN connection.
In the Add a VPN connection dialog:
- VPN provider: Set to Windows (built-in)
- Connection name: This can be anything you want to name this connection, for example, 'Work VPN.'
- Server name or address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- VPN type: Select L2TP/IPsec with pre-shared key
- User name and Password: optional
Press Save.
After the VPN connection has been created, click Change adapter options under Related settings.
Right-click on the VPN Connection from the list of adapters and click Properties.
Despite the name 'Unencrypted PAP', the client's password is sent encrypted over an IPsec tunnel between the client device and the MX. The password is fully secure and never sent in clear text over either the WAN or the LAN.
In Advanced Properties dialog box, choose 'Use preshared key for authentication' and enter the pre-shared key that admin created in Security appliance >Configure > Client VPN settings.
Back at the Network Connections window, right-click on the VPN connection and click Connect / Disconnect.
Find your VPN profile and click Connect.
Windows XP
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, use the email address for VPN account / user name.
Open Start Menu > Control Panel, click on Network Connections.
In the Network Tasks section, click on Create a new connection.
Choose Connect to the network at my workplace, in the New Connection Wizard window.
Choose Virtual Private Network connection in the next section.
Then, give a name for this connection. This can be anything you want to name this connection, for example, 'Work VPN.'
Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
In the Connect box, click on Properties
In the General tab, verify the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
Despite the name 'Unencrypted PAP', the client's password is sent encrypted over an IPsec tunnel between the client device and the MX. The password is fully secure and never sent in clear text over either the WAN or the LAN.
A Vpn For Kodi
Linux
Mac Vpn Download
Since Client VPN uses the L2TP over IPsec standard, any Linux client that properly supports this standard should suffice. Please note that newer versions of Ubuntu do not ship with a VPN client that supports L2TP/IP, and will therefore require a 3rd party VPN client that supports the protocol.
How To Configure A Vpn For Mac
Note: The xl2tp package does not send user credentials properly to the MX when using Meraki Cloud Controller authentication, and this causes the authentication request to fail. Active Directory or RADIUS authentication can be used instead for successful authentication.